Cybersecurity Risk Assessments
Be proactive in your cyber security protection against malware and hackers
Just because your business has had a year without any cybersecurity breach doesn`t mean you will always be so fortunate. Hackers and malware are becoming ever more rampant and sophisticated, increasingly targeting the low-hanging fruit -- small and medium-sized businesses because of their low IT Cyber Security maturity levels. In this field the ground shifts often and quickly, what was fine 3 years ago can be quite obsolete or even become an actual vulnerability liability today. Don’t wait for an intrusion to happen before putting up safeguards.
When was the last time you had a Vulnerability Scan or a Penetration Test conducted on your environment?
Security Risk Assessments
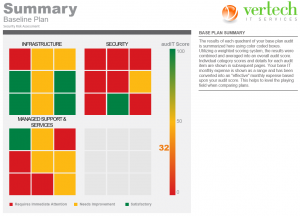
We offer two types of audits:- The Free Quick "Hands Off" systems check - This cyber security consulting is suitable for a smaller business with limited complexity where the owners are already aware there a some problems to be fixed. We send out two team members for an hour, one to interview the main technical point of contact or decision maker in the organisation and another to visually inspect the network, systems and passively obtain information through various means. A simple traffic light report is generated and Vertech's remediation/mitigation costs provided. Due to resource constraints we can only provide a small amount of these per quarter however to apply please fill the form below and we shall contact you to discuss.
- The Paid "Thud Factor" Full Risk Assessment & Report - Costing upwards of $3970 depending on your company size and complexity we will conduct a formal assessment utilising the CIS/SANS 18 v8 Security Framework to examine your environment from within & without whilst looking at factors such as People, Processes and Protections. We interview the management as well as staff, run credentialed vulnerability scans internally and external scans against any public facing systems such websites & firewalls. The information is gathered into a final report where the risks are prioritised by priority and potential impact to the business with the mitigation strategies and estimated costs provided such that you can hand the plan to your inhouse or existing IT provider to resolve.
Settling for the bare minimum in your cybersecurity strategy won’t protect you effectively.
It goes way beyond Antivirus & Spam Filtering and it is an iterative process with a Security Risk Assessment setting a baseline for an annual review to make sure you are staying on top of your game.
You may need vCSO (virtual Chief Security Officer) service to ongoingly improve your cyber security systems and we are able to support your business management and board decisions by providing appropriately skilled & experienced consultants to advise you on an ongoing basis which may be as little as 2 hours per month. Ongoing cyber security support for your systems can be provided in the form of network security services for your business such as managed firewall and managed network services where the entire solution hardware, security subscriptions, maintenance and support are all included. We align our services with the CIS (Center for Internet Security) controls as they are an independent open set of standards that allow for the needs and capabilities of small, medium and enterprise classes of businesses. The framework allows us to provide actionable recommendations that are practical in terms of protecting businesses from the current extant threats. A business that we engage with on a flat rate plan and takes up our full security stack will also receive our unique 100% money Back Cyber Security Guarantee!ISO 27001 Information Security Management Systems
If you are an exporter to the the EU or do you deal with defense and medical industries in the USA? We have staff who are certified to both independently Audit and act as Lead Implementers of your organisation's effort to become ISO certified..GDPR and Privacy regulatory Compliance
- Do you need a GDPR compliance roadmap report (prioritised list of actions for GDPR compliance)?
- Have you set a Privacy policy and cookies policy for your website?
- Have you thought about getting a detailed review of your website and other on-line presences and including a review of links to privacy policy, notice of collection, consent to marketing, cookies being used etc.
- Privacy Officer services – we can help give you access to a privacy officer (required for EU) and the provision of privacy assistance. This can include privacy training, policy development, responding to client requests etc.
Comprehensive Cyber Security Services
Anti-virus, anti-malware, EDR, Ransomware and Advanced Threat Protection, Managed Firewalls with Intrusion Detection, file disk and email encryption, Mobile Device Management, Domain credential monitoring for password exposure, Azure Multi Factor Authentication (MFA), Data Loss Prevention, Vulnerability and Patch Management, Archiving and Backups, Offsite Rapid Disaster Recovery. IT Governance and policy Creation.

She'll Be Right (Not!):
A Cybersecurity Guide for Kiwi Business Owners
Got this far?
SHHH! Here's a Secret! If you fill out this form and Daniel catches up with you, he'll probably give your own signed copy for Free!
Got this far?
SHHH! Here's a Secret! If you fill out this form and Daniel catches up with you, he'll probably give your own signed copy for Free!
